
About this article: This article is a source of reference information related to challenges that institutions of higher education experience. While large universities may have advanced information security systems this document can serve as reinforcement information to those systems. It can also serve as a starting point for identifying best practices for smaller universities and colleges.
The Challenge
Colleges and universities across the US by their nature are open campuses of learning. Campuses, where thousands of students can access seemingly unlimited scholarly resources and where internet information flows freely. These campuses are places where massive amounts of information are collected, studied, and researched. This information should not be accessible to the public. The collision of these information systems creates a nebulous structure where rules of data classification can range from public, private, and restricted including top-secret. While struggling with data classification these institutions are also expanding into the foggy potential of cloud services. How can these institutions protect the existing systems and prepare for the unknown vulnerabilities and future exploits?
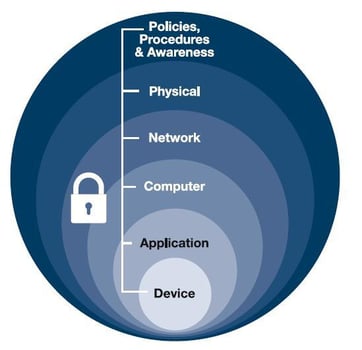 Defense in Depth
Defense in Depth
A fundamental concept of information security is derived from military strategy, defense-in depth. Originally conceived by the National Security Agency (NSA) defense in-depth, simply means overlapping layers of protection through the controls. These controls fall in three areas physical, technical, and administrative. The most mature control in defense in depth is physical controls. Physical controls have been around before modern information systems. They are well known and ubiquitous in the industry; however technical and administrative controls are less mature and continually meeting new challenges. Anyone using a smart device, laptop, or PC is familiar with the terms antivirus, strong passwords, two-factor authentication, backdoor, firewalls, virtual private networks (VPN), and encryption. These terms are common with our technical lives and can be heard on almost any modern show or movie. There are also lesser-known terms such as threat actor, supply chain attacks, credential stuffing, and social engineering that keep security professionals up a night. These threats do not manifest in the form of a visual attack but are designed to sneak into systems slowly and deliberately. The goal behind these attacks is not to shut down or overwhelm a system but it is to gather information. Information that can be used for future gain through espionage, blackmail, or by simply selling the information. Building a strategy of defense in depth greatly bolsters the system protections but threat actors using a vast array of tools may not come in through the traditional means. With a defense-in-depth strategy in place what more should be done? This is where Security System Engineering can come to aid. Security System Engineering
System Security Engineering v(SSE) is a specialty security engineering defined by the US Department of Defense as "an element of system engineering that applies scientific and engineering principles to identify security vulnerabilities and minimize or contain risks associated with these vulnerabilities" (DODI5200.44, 12). SSE is taking information security to the next level of protection by building a resilient system that remains secure through effects of malice or mistake. There are many principles and domains to the implementation of SSE and it requires a comprehensive security view of all systems that starts from the birth of a solution until retirement. SSE takes the layered approach of defense of depth and enhances physical, technical, and administrative layers. The expansion of the layers accounts for external influences that come from compliance requirements, staffing competency, or process management. SSE’s thorough approach can be often overwhelming and reading the information alone requires a significant time investment.
Solutions for Institutes of Higher Education
University and colleges are skilled at building systems around the students. They offer single sign-on (SSO) and account authentication that follows the students from system-to-system. They also build powerful networks to serve the student population. These networks offer high bandwidth and are built around well-known secure equipment such as Cisco, Juniper, Dell, and Aruba. They also use the top-named firewalls such as Palo Alto, Cisco, Fortinet, or Juniper. These networks are well designed, secured uses VLANs or other means of segmentation at the network level. They are designed to be secure, but what about the devices using the network? Education institutions might have 10s of thousands or over 100 thousand endpoints accessing the campus network. This is when a robust endpoint detection and response (ERD) solution with a high MITRE evaluation should be implemented. Products such as CrowdStrike Falcon or VMWare Carbon Black often meet the customer’s needs and implementing a campus-wide initiative to deploy advanced EDRs creates the first line of defense. With the initial defense-in-depth in place, what more can be done? This is where the next steps can be taken, and security system engineering (SSE) enhances existing systems. The goal of SSE is to achieve system assurance for all layers of protection. Universities with thousands of endpoints should understand the normal behavior on their network. It is a priority to understand the behavior of the internal and 3rd party applications. Insight across the network should be the Universities' goal. This is where a Managed Detection and Response (MDR) system could be implemented. An MDR such as Securework’s Red Cloak TDR uses artificial intelligence, deep learning, and behavioral analytics to rapidly detect threats. A comprehensive MRD will prioritize activities from the endpoints, networks, and cloud system to identify threats and recommend remediation. MDRs will recognize the credential stuffing behavior, recognize the rogue application, or even the slow leakage of data to foreign websites. An MDR provider such as Secureworks, will also provide readily accessible experts and the ability to engage a support team 24x7. They will be there to understand the motivation of the threat actor, and they can recommend steps to limit the damage of the compromised system. Partnering with the right MDR provider will allow the security professionals to sleep peacefully knowing their systems are ready to respond to a threat.
Getting Results
Equipped with this knowledge you can focus on bringing the right resources to your institution. Summus Industries joined the Secureworks Global partner program to offer automated and intelligent cybersecurity solutions that secure progress with Managed Detection and Response (MDR). Summus Industries can help coordinate these activities and become an extension of your workforce. We can manage the process of engaging Dell Technologies and bring solutions from Secureworks and VMWare to you Streamlining costs is more important than ever we can extend our financial arm through Summus Leasing to get you the solution today.
If you're interested in how MDR can help your organization, please connect with our sales team here.
References:
Secureworks Managed Detection and Response Data Sheet:
https://www.secureworks.com/resources/ds-managed-detection-and-response
CrowdStrike vs Carbon Black: Top EDR Solutions Compared
https://www.esecurityplanet.com/products/crowdstrike-vs-carbon-black/
Recommended Practice: Improving Industrial Control System Cybersecurity with Defense-in-Depth Strategies
https://us-cert.cisa.gov/sites/default/files/recommended_practices/NCCIC_ICS-CERT_Defense_in_Depth_2016_S508C.pdf



